Tech
Smart IoT Gateway: The Future of Network Connectivity
As the world becomes more connected, the need for reliable and secure network connectivity has never been greater. Enter MEF 3.0 Ethernet demarcation and Smart IoT Gateway technology – two game-changing solutions that are transforming the way we think about network infrastructure. In this blog, we delve into the benefits of these cutting-edge technologies and explore how they’re shaping the future of network connectivity.
The world of connected devices is expanding unprecedentedly, and traditional network infrastructure needs help to keep up with the sheer volume of data generated by these devices. Service providers are turning to advanced technologies like MEF 3.0 Ethernet demarcation and Smart IoT Gateway to facilitate seamless connectivity and ensure reliable performance. These powerful solutions provide a variety of advantages for organizations trying to capitalize on the Internet of Things (IoT) boom, ranging from greater network monitoring capabilities to better device management and faster data transfer.
Ethernet Demarcation: Essential for Service Providers
Ethernet demarcation is one of the most important concepts in modern networking infrastructure. Simply, it refers to when a service provider’s network ends and the customers begin. This demarcation point is critical for ensuring that both parties understand their responsibilities regarding managing connectivity and resolving any issues.
For service providers, Ethernet demarcation provides a clear boundary between their network infrastructure and their customers. By defining this boundary, they can ensure that all data traffic flows smoothly across the network without interference or interruption from external sources.
In addition to providing clarity around responsibility for network management, Ethernet demarcation also enables service providers to monitor performance more effectively. They can use advanced tools like OAM (Operations, Administration, and Maintenance) to detect and proactively address issues before they become significant problems.
MEF 3.0 Framework and Its Significance
The MEF 3.0 framework is a set of global standards that defines the requirements for providing assured services over automated networks. It enables service providers to offer agile, assured, and orchestrated connectivity services that meet the demands of today’s digital economy.
MEF 3.0 provides a comprehensive set of technical specifications and implementation agreements that ensure interoperability among different vendors’ equipment and software solutions. This allows service providers to deploy new network services while reducing complexity and costs efficiently.
One of the key benefits of MEF 3.0 for service providers is its emphasis on delivering end-to-end network visibility, control, and automation capabilities across multiple technology domains (e.g., MPLS, Ethernet, IP). By adopting MEF 3.0-compliant solutions, service providers can better serve their customers with more predictable performance levels while simplifying operations through automation.
The introduction of MEF 3.0 has enabled service providers to modernize their networks by moving towards a more flexible and scalable infrastructure capable of meeting growing bandwidth demands from cloud-based applications and emerging technologies such as IoT devices.

Benefits of Ethernet Demarcation
Ethernet demarcation is an essential tool for service providers, allowing them to provide reliable network connectivity while also ensuring the security and integrity of their customer’s data. One of the critical features of Ethernet demarcation is advanced OAM (Operations, Administration, and Maintenance) capabilities that help service providers quickly identify and resolve issues on their networks.
With Ethernet demarcation, service providers can monitor network performance in real time, proactively identifying potential issues before they become significant problems. This ensures that customer connections are always up and running and helps service providers improve the overall performance of their networks.
Another benefit of Ethernet demarcation is its ability to isolate traffic from different customers or applications, ensuring that sensitive information remains secure at all times. This feature helps businesses maintain compliance with industry regulations such as HIPAA or PCI-DSS.
Ethernet demarcation provides numerous benefits for both service providers and their clients. Organizations may maintain optimal network performance while preserving the privacy and security of sensitive data by allowing enhanced OAM capabilities and real-time network monitoring.
Smart IoT Gateway and its Role in Enabling IoT Connectivity
Smart IoT Gateway is a crucial component in enabling seamless IoT connectivity. As the amount of connected devices increases, so does the requirement for a gateway to properly manage and route data.
A Smart IoT Gateway acts as an intermediary between the cloud and edge devices, providing a secure connection for data transmission. It allows different types of sensors and devices with varying communication protocols to communicate with each other without any issues.
Moreover, Smart IoT Gateways has advanced features such as protocol translation, data filtering, security management, and analytics capabilities. These features help organizations optimize their networks by reducing latency and bandwidth consumption.
Organizations can reduce network complexity by consolidating multiple functions into one device by using a Smart IoT Gateway. This not only simplifies network infrastructure but also reduces maintenance costs significantly.
Smart IoT Gateways enable efficient and effective communication between edge devices and the cloud. With its advanced features like protocol translation and security management combined with MEF 3.0 Ethernet demarcation standards – it’s no surprise that this technology represents the future of network connectivity.
Enabling Seamless Network Connectivity
MEF 3.0, Ethernet demarcation, and Smart IoT Gateway are three key components that work together to enable seamless network connectivity in the age of the Internet of Things (IoT).
MEF 3.0 provides a framework for providers to deliver secure services across automated networks. This framework helps service providers meet the demands of an increasingly connected world while ensuring security and reliability.
Ethernet demarcation is essential for service providers because it allows them to define where their responsibility ends and their customer’s responsibility begins. With advanced OAM (Operations, Administration, and Maintenance) features, Ethernet demarcation enables real-time network performance monitoring to identify and resolve potential issues quickly.
Smart IoT Gateway is vital in enabling IoT connectivity by providing secure communication between devices on different networks. It acts as a bridge between disparate systems, translating protocols and formats so that data can flow seamlessly from one device or system to another.
Together, MEF 3.0, Ethernet demarcation, and Smart IoT Gateway provide a comprehensive solution for delivering high-quality network services with end-to-end visibility into performance metrics. These technologies work in tandem to ensure reliable connections between devices regardless of location or protocol used, leading to more efficient operations within businesses using such technology stacks.
The Future of Smart IoT Gateways
Smart IoT gateways are the future of network connectivity and will only become more advanced in the coming years. As IoT devices proliferate across businesses and homes, smart gateway technology will play an even more significant role in enabling seamless connectivity.
One area where we can expect significant growth is edge computing capabilities. Smart IoT gateways have already begun incorporating powerful processing capabilities that allow them to perform complex computations at the network’s edge. These gateways will become even more sophisticated in the future, with machine learning algorithms built-in for real-time data analysis.
Another critical trend is increased interoperability between different types of devices and networks. With standards like MEF 3.0 providing a framework for consistent service delivery across disparate networks, we can expect smart IoT gateways to play a crucial role in seamlessly connecting these various systems.
As security concerns continue to grow around connected devices and networks, smart IoT gateways will become increasingly important in securing these environments against potential threats. With advanced features like secure boot firmware and hardware encryption already becoming standard on many gateway models today, it’s clear that this trend towards improved security will only accelerate over time.
The future of network connectivity is looking brighter thanks to the advancements made in MEF 3.0, Ethernet demarcation, and Smart IoT Gateway technology. These technological innovations enable service providers to offer more robust and reliable services to keep up with the ever-increasing demands of today’s businesses.
Ethernet Demarcation provides essential features such as advanced OAM and network performance monitoring, allowing service providers to maintain their networks effectively. On the other hand, Smart IoT Gateway enables seamless connectivity across various devices in an Internet of Things (IoT) ecosystem.
As more businesses adopt IoT technology into their operations, it becomes crucial for service providers to deliver a reliable and dependable network experience for these organizations. MEF 3.0 framework ensures interoperability between different vendors’ equipment used by Service Providers within this new world of Network Technology.
These technological advancements will continue shaping the future of networking as we know it by providing better reliability and greater scalability at reduced costs than before!
Article FAQs
What is MEF 3.0, and why is it necessary for network connectivity?
Answer: MEF 3.0 is a set of standards and specifications for Carrier Ethernet services. MEF 3.0 is necessary for network connectivity because it provides a framework for delivering Carrier Ethernet services with outstanding performance, reliability, and scalability. It enables service providers to offer their customers agile, assured, and orchestrated services.
What is Ethernet demarcation, and how does it help service providers?
Answer: Ethernet demarcation is when the service provider’s responsibility for the Ethernet service ends and the customer’s responsibility begins. Ethernet demarcation devices help service providers manage and monitor Ethernet services at the demarcation point. They provide advanced OAM and network performance monitoring capabilities, enabling service providers to troubleshoot issues and ensure service quality.
What is a Smart IoT Gateway, and how does it enable IoT connectivity?
Answer: A Smart IoT Gateway is a device that enables connectivity between IoT devices and the cloud or data center. It bridges the IoT devices and the network infrastructure, allowing data to be transmitted securely and efficiently. Smart IoT Gateways are designed to be low-power, compact, and capable of remote management, making them ideal for IoT applications.
How do MEF 3.0, Ethernet demarcation, and Smart IoT Gateway work together to enhance network performance?
Answer: MEF 3.0 provides a standardized framework for Carrier Ethernet services, enabling service providers to deliver high-performance and reliable connectivity. Ethernet demarcation devices help service providers manage and monitor Ethernet services, ensuring they meet the required performance levels. Smart IoT Gateways enable secure and efficient connectivity between IoT devices and the network, enhancing the network’s overall performance.
What are some practical examples of successful technology integration?
Answer: One example is a healthcare organization that used MEF 3.0, Ethernet demarcation, and Smart IoT Gateway to connect medical devices and patient data to the cloud. The MEF 3.0 framework enabled the healthcare organization to deliver high-performance and reliable connectivity, while Ethernet demarcation devices provided advanced OAM and network performance monitoring capabilities. Smart IoT Gateways enabled secure and efficient connectivity between medical devices and the cloud, ensuring patient data was transmitted securely and efficiently.
3D Technology
Automotive PCBs: Engineering Reliability for the Era of Autonomous and Electric Vehicles
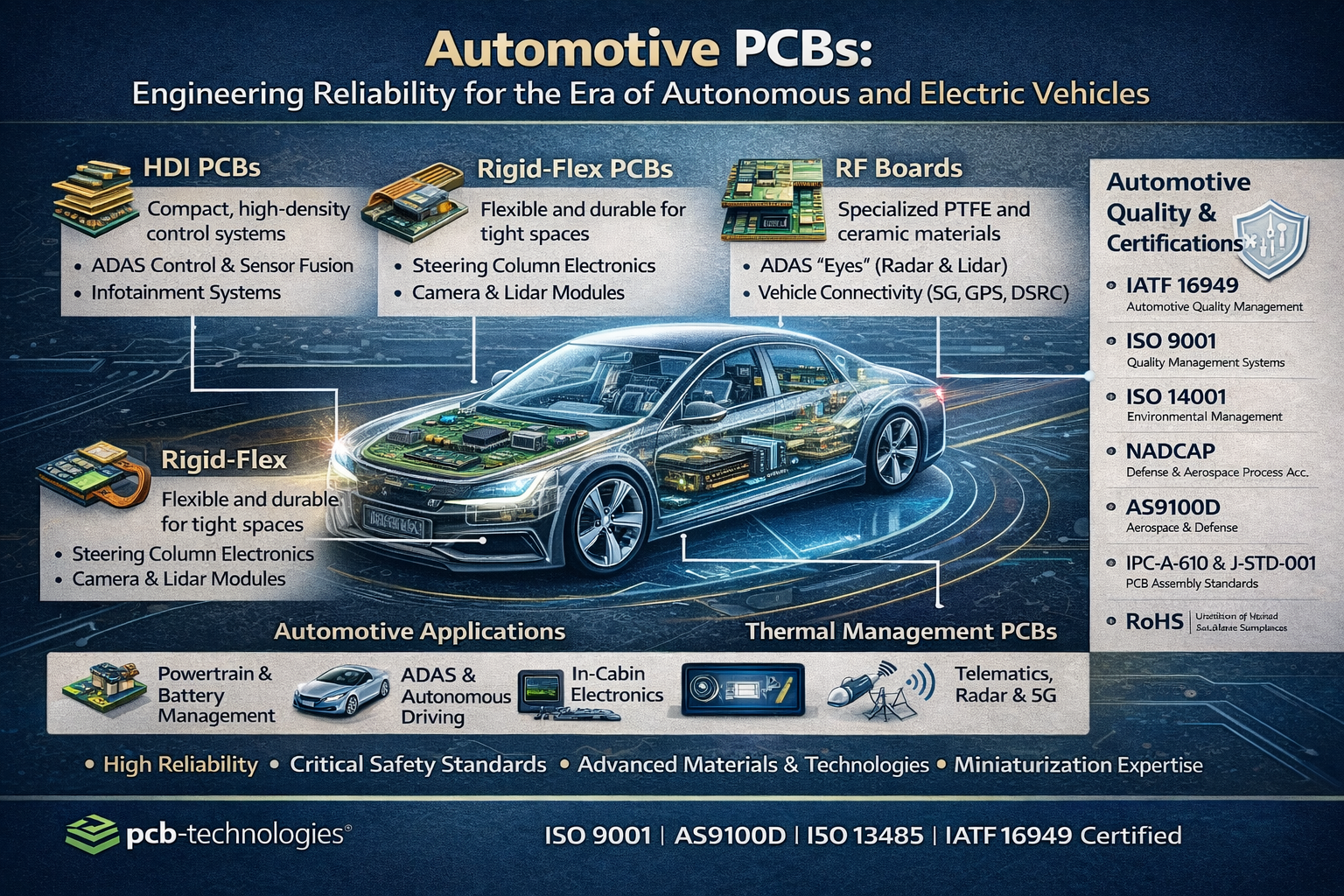
The modern automobile is no longer simply a mechanical machine. Today’s vehicles — whether a conventional combustion engine car, a battery electric vehicle (BEV), or a fully autonomous system — are deeply sophisticated electronics platforms. Every function, from the engine management system and power steering to the infotainment screen and lidar sensor array, depends on printed circuit boards engineered to perform reliably across extreme temperature ranges, severe vibration, and decades of continuous operation.
Automotive PCBs are among the most demanding products in the electronics manufacturing industry. Failure is not an option: a board that malfunctions in an automotive safety system can have life-altering consequences. This article explores the technology, standards, and applications that define automotive PCBs — and explains why pcb-technologies is a trusted supplier to OEMs and their Electronic Manufacturing Services (EMS) providers worldwide.
Why Automotive PCBs Are Different
Automotive electronics must operate across temperature ranges from -40°C to 85°C or beyond, withstand continuous vibration and mechanical shock, resist moisture and chemical exposure, and maintain full performance for 15+ years of vehicle lifetime. Standard commercial PCBs are not designed for these demands.
The transition to electric and autonomous vehicles has intensified these requirements. New automotive PCB challenges include:
- Power electronics for EV drivetrains: High-current boards managing hundreds of amperes and hundreds of volts for motor inverters and charging systems
- AI processors for autonomous driving: Boards supporting AI accelerators (GPUs, TPUs) with Ball Grid Array packages requiring fine lines, micro-vias, and ultra-low-loss materials for data rates exceeding 25 Gbps
- Lidar and radar modules: High-frequency RF boards requiring specialized PTFE or ceramic-based laminates to maintain signal integrity at millimeter-wave frequencies
- ADAS sensor fusion: Multiple sensor types (radar, lidar, cameras, ultrasonic) integrated through high-density PCB interconnects
- In-cabin electronics: Touchscreens, heads-up displays, driver monitoring systems — all requiring compact, reliable PCBs
Types of PCBs Used in Automotive Applications
pcb-technologies supplies multiple PCB types tailored to the specific demands of automotive electronics:
HDI PCBs (High-Density Interconnect)
HDI PCBs are ideal for automotive control technology, with the ability to pack more functionality into a smaller, lighter footprint. In an industry where size and weight are critical for fuel efficiency and EV range, HDI technology uses micro-vias and fine lines to enable complex, multi-layered designs that would be impossible on conventional boards. pcb-technologies produces HDI boards using the Excellon Cobra Hybrid Laser system and X-VIA technology for precise, void-free via structures.
Rigid-Flex PCBs
Combining the durability of a rigid board with the flexibility of a flex circuit, rigid-flex PCBs are perfect for automotive applications that require a design fitting into tight or irregularly shaped spaces — such as steering column electronics, dashboard assemblies, and camera modules in door mirrors. Rigid-flex eliminates the need for bulky connectors and wire harnesses, reducing both weight and failure points.
RF Boards (Radio Frequency)
Modern vehicles depend on a growing number of RF systems: GPS, V2X (vehicle-to-everything) communications, LTE/5G telematics, radar-based ADAS systems, and keyless entry. RF boards require specialized materials like PTFE or ceramic-based laminates to maintain signal integrity and minimize loss at high frequencies. pcb-technologies has extensive expertise in RF board design and fabrication.
Thermal Management PCBs
Automotive electronics impose significant thermal loads, particularly in power electronics for EVs and high-performance engine control units. pcb-technologies combines materials science, mechanical engineering, and PCB manufacturing technology to effectively dissipate heat. Solutions include embedded copper coins, thermal vias, metal-core boards, and specialized thermally conductive laminates.
Automotive Quality Standards: IATF 16949 and Beyond
The automotive industry operates under some of the strictest quality management requirements in any sector. The key standard is IATF 16949, which defines quality management system requirements specifically for the design, development, production, installation, and service of automotive-related products.
pcb-technologies is certified to IATF 16949, along with a comprehensive suite of additional certifications relevant to automotive customers:
- IATF 16949 — Automotive quality management system
- ISO 9001 — General quality management
- ISO 14001 — Environmental management
- NADCAP — Defense and aerospace process accreditation (for defense-grade automotive programs)
- AS9100 — Aerospace quality management (relevant for autonomous vehicle programs with aerospace-grade requirements)
- RoHS Lead-Free compliance — Fully compliant with automotive RoHS requirements
- IPC-A-610 and J-STD-001 — Assembly standards for all PCBA
pcb-technologies’ Automotive PCB Capabilities
With over 40 years of experience in high-reliability PCB manufacturing, pcb-technologies has built a well-earned reputation in the automotive sector. Key capabilities include:
- Full design services: From initial schematic through DfM, DfT, DfP, DfC, and DfA analysis — optimized for automotive quality and cost targets
- Advanced materials: Including Rogers laminates, PTFE, polyimide, and metal-core for specific automotive performance requirements
- High-current PCBs: Supporting relay and fuse boxes, DC/DC converters, inverters for EV systems, and power/signal integration on one board
- PCBA with advanced packaging: Including Package-on-Package (POP), Micro BGAs, and IC packaging services through the iNPACK division
- Comprehensive testing: ICT, AOI, functionality testing, and vibration testing (S452 Electrodynamic Shaker) — critical for automotive reliability validation
- NPI (New Product Introduction): Fast-tracked NPI services supporting rapid development cycles typical in automotive Tier 1 and OEM programs
The Road Ahead: Automotive Electronics Trends
The automotive PCB market is in the midst of a fundamental transformation, driven by electrification and autonomy:
- Software-defined vehicles: Central computing architectures replacing distributed ECUs, requiring fewer but more powerful, high-density PCBs
- V2X (Vehicle-to-Everything): PCBs supporting 5G NR and DSRC communication modules for cooperative driving
- Integrated AI at the edge: Boards with AI accelerators running machine learning models for real-time visual quality control and autonomous decision-making
- Wearable and in-cabin electronics: Flexible and rigid-flex PCBs enabling new form factors for driver and passenger interfaces
- Battery Management Systems (BMS): High-reliability, high-current boards for EV battery pack management
pcb-technologies is positioned to serve all these emerging requirements, with its iNPACK miniaturization platform and comprehensive design-to-production capability ready for the automotive industry’s next decade.
Learn more about pcb-technologies’ automotive PCB solutions at automotive industry page.
Explore the iNPACK division for advanced packaging in automotive applications at pcb-technologies iNPACK.
Return to the pcb-technologies homepage at pcb-technologies.com.
Frequently Asked Questions
Q: What certifications does pcb-technologies hold for automotive PCBs?
A: pcb-technologies is certified to IATF 16949 (automotive), ISO 9001, ISO 14001, NADCAP, AS9100, and RoHS. All assembly is performed by IPC-A-610 and J-STD-001 certified experts.
Q: What types of PCBs are used in electric vehicles?
A: EV applications use HDI PCBs (for ADAS and control electronics), RF boards (for telematics and radar), thermal management PCBs (for power electronics and battery management), rigid-flex PCBs (for compact form factors), and high-current boards for inverters, converters, and battery management systems.
Q: Why is thermal management critical for automotive PCBs?
A: Automotive electronics generate significant heat, especially in EV power electronics and AI processors. Boards that cannot dissipate heat reliably will fail prematurely — a safety-critical issue. Thermal management solutions include embedded copper coins, thermal vias, metal-core boards, and specialized laminates.
Q: What is IATF 16949 and why does it matter?
A: IATF 16949 is the international automotive quality management standard. It covers design, development, production, installation, and service of automotive-related products. Automotive OEMs and Tier 1 suppliers typically require their PCB manufacturers to be IATF 16949 certified.
Q: Can pcb-technologies produce automotive PCB prototypes as well as production volumes?
A: Yes. pcb-technologies supports the full product lifecycle — from NPI prototype through low, mid, and high volume production — all with the same quality standards and certifications.
Marketing & Analytics
Why Israeli Tech Startups Cannot Afford to Wait on SEO and GEO

There is a common misconception among early-stage technology startups: that digital marketing — and search optimization in particular — is something you invest in once you have achieved product-market fit, closed a Series A, and built out your marketing team. In the meantime, you focus on the product, the pitch, and the first customers.
This reasoning is understandable. It is also strategically dangerous.
In a B2B technology landscape where 91% of buyers now use AI tools in their purchase process, and where competitors are investing in search visibility from their earliest days, the decision to defer digital marketing is not neutral. It is a decision to start from behind. Domain authority, topical expertise signals, and AI citation presence all take time to build — and that time is not recoverable.
Inter-Dev has been working with Israeli startups and scale-ups since 2007, helping them build powerful digital foundations that generate early traction, attract investor attention, and prepare them for scalable international growth. As Israel’s leading B2B digital marketing agency — recognized as a Top 3 SEO Agency in the country with awards from Clutch, 50 Pros, and The Manifest — Inter-Dev brings nearly two decades of startup-specific experience to this challenge.
The Startup SEO Imperative: Why Early Action Compounds
Search engine optimization is one of the few marketing channels where early investment creates lasting compounding returns. Every piece of content published, every technical improvement made, every backlink earned contributes to a cumulative authority signal that grows over time. A startup that begins building this foundation in year one will have a structural SEO advantage over a competitor that starts in year three — an advantage that is very difficult for the late mover to close.
For Israeli startups targeting international markets, this compounding logic is amplified. Building domain authority and topical expertise for highly competitive B2B technology categories in markets like North America requires sustained effort over time. The earlier you start, the more cost-effective the path to competitive visibility becomes.
Inter-Dev’s startup engagements are designed around this reality. Rather than deploying generic marketing tactics, the agency works with founding and marketing teams to define a go-to-market search strategy from day one — establishing the right topical focus, building content that speaks to early-stage buyer intent, and laying the technical foundations that will scale as the company grows.
The New Discovery Landscape: Why Startups Must Consider GEO From the Start
The rise of generative AI search has created both a challenge and an opportunity for startups. The challenge: AI systems tend to recommend established, well-documented brands with strong authority signals — which works against early-stage companies. The opportunity: the AI discovery landscape is itself still young, and startups that invest in GEO early can establish a foothold in AI-generated recommendations before their competitors have even started.
Inter-Dev’s AI Search & Discovery practice includes specific services designed to help startups build AI visibility from the ground up:
- Technical AI Readiness: Ensuring the startup’s website and content assets are fully accessible and accurately represented by AI crawlers from launch.
- Entity establishment: Building the structured data and external signals needed for AI systems to recognize the startup as a credible, defined entity in its market category.
- Content authority: Developing high-quality, publicly accessible thought leadership content that AI systems can cite — not gated assets that disappear behind lead capture forms.
- Competitive positioning: Using AI competitive analysis to identify the gaps in how AI systems currently represent the market, and positioning the startup to fill them.
The connection to content strategy is direct. Inter-Dev’s latest blog post — ‘From Gated to Ghosted: The High Cost of Blocking AI from Your Best Specs’ — addresses this challenge directly, arguing that startups and established companies alike are making a critical mistake by locking their best content behind forms. For a startup trying to build AI visibility, freely accessible, technically credible content is not just a nice-to-have — it is the primary mechanism by which AI systems learn about your brand.
Building a Go-to-Market Digital Strategy for Startups
What does a practical startup digital marketing engagement with Inter-Dev look like? The approach is built around the specific growth stage and objectives of each company, but typically encompasses four integrated areas:
1. Digital Foundation and Technical SEO
Before any content is created, the technical substrate must be correct. This includes site architecture designed for search crawlability, page speed optimization for Core Web Vitals compliance, structured data implementation for entity recognition, and clean internal linking structures that help both search engines and AI systems understand the relationship between pages and topics.
2. Topical Authority Strategy
Rather than attempting to rank for generic keywords against well-resourced established competitors, Inter-Dev helps startups identify the specific niche topics and intent categories where they can credibly establish authority quickly. This targeted approach maximizes early SEO gains and creates the topical concentration that AI systems reward with citation authority.
3. Content for AI-Mediated Buyers
The B2B content strategy for a startup in 2025 and beyond must be built for two audiences simultaneously: human buyers who want technical credibility and clear value propositions, and AI systems that need structured, accessible content to form accurate opinions about your brand. Inter-Dev’s content approach, developed over years of working with technology companies, is designed to serve both audiences without compromise.
4. Paid Campaigns for Immediate Visibility
While organic SEO and GEO build over time, startups often need immediate visibility to support sales cycles and investor narratives. Inter-Dev’s performance marketing practice delivers targeted paid campaigns across Google, LinkedIn, and other B2B-relevant platforms that generate qualified leads while the organic foundation is maturing. The integration of paid and organic strategy under one agency ensures consistency of message and efficient budget allocation.
Why Israeli Startups Choose Inter-Dev
The answer lies in a rare combination: deep specialization in B2B technology marketing, intimate knowledge of the Israeli startup ecosystem, and genuine expertise in the international markets where Israeli companies need to compete.
Inter-Dev has worked with startups across semiconductor, SaaS, cybersecurity, medical devices, and other high-growth technology sectors. The agency understands the specific pressures that startup marketing teams face: limited budgets, lean resources, the need to demonstrate marketing ROI to investors, and the complexity of simultaneously building a brand and generating pipeline in markets you may not be physically present in.
The testimonials from clients like Hailo, LiveU, and PlaxidityX speak to a consistent pattern: Inter-Dev functions not as a vendor but as an extension of the client’s marketing team — providing senior-level strategic guidance, transparent performance reporting, and the kind of collaborative engagement that produces real business outcomes.
For startups ready to build a powerful digital foundation, Inter-Dev’s B2B marketing for startups practice offers a proven path from early-stage digital presence to scalable international visibility.
To understand the full AI Search Optimization toolkit that Inter-Dev brings to startup engagements, explore the AI Search Optimization services — and discover how GEO can be built into your go-to-market strategy from day one.
Visit the Inter-Dev homepage to explore the complete range of services and request a strategic consultation for your startup.
Frequently Asked Questions
Is Inter-Dev suitable for very early-stage startups?
Yes. Inter-Dev has a specific practice for B2B startup marketing, designed to meet early-stage companies where they are. The focus is on building a strong digital foundation that generates initial traction and prepares for scalable growth — with strategies tailored to the constraints of a startup budget.
When should a startup start investing in SEO?
As early as possible. SEO authority compounds over time, and every month of delay means ceding ground to competitors who started earlier. At minimum, the technical SEO foundations should be correct from the moment the website launches.
Can a startup benefit from GEO at an early stage?
Yes — and arguably, early-stage companies benefit most from GEO because the AI discovery landscape is still forming. Startups that invest in AI visibility early can establish a presence in AI-generated recommendations before their market position is fixed in the minds of AI systems.
How does Inter-Dev handle the challenge of limited startup marketing budgets?
Inter-Dev tailors engagement models to the specific growth stage of each client. For startups, the focus is on the highest-leverage activities: technical foundation, topical authority in a defined niche, and targeted paid campaigns that generate immediate pipeline while organic authority builds.
Does Inter-Dev work with startups targeting international markets?
Yes. Inter-Dev has a global-first mindset and deep expertise in foreign market penetration — particularly North America and Europe, which are the most important international markets for most Israeli tech startups. The agency provides multilingual capabilities and international market knowledge built over 17 years.
Business Solutions
Drone-UAV RF Communication: The Backbone of Modern Aerial Operations
Drone-UAV RF Communication is revolutionizing the way drones operate, serving as the foundation for reliable, efficient, and innovative aerial systems. From ensuring seamless connectivity to enabling advanced maneuvers, this technology plays a pivotal role in modern drone operations. Its ability to provide consistent and secure communication is what makes it indispensable for both commercial and defense applications.

Unmanned Aerial Vehicles (UAVs), commonly known as drones, have become a pivotal technology across industries such as defense, agriculture, logistics, and surveillance. At the core of a drone’s functionality is its communication system, which enables control, data transfer, and situational awareness. Radio Frequency (RF) communication plays a crucial role in ensuring that UAVs can operate effectively in a variety of environments, with high reliability and low latency. Learn more about DRONE-UAV RF COMMUNICATION.
This article delves into the significance of RF communication in Drone-UAV operations, the challenges it presents, the technologies involved, and how future advancements are shaping the communication systems for UAVs.
The Role of RF Communication in Drone-UAV Operations
RF communication is the medium through which most drones communicate with ground control stations (GCS), onboard systems, and other UAVs in a network. It enables the transmission of various types of data, including:
Control Signals: These are essential for operating the UAV, including commands for takeoff, landing, navigation, and flight adjustments.
Telemetry Data: Real-time data on the UAV’s performance, including altitude, speed, battery level, and sensor readings.
Video and Sensor Data: Drones equipped with cameras or other sensors (such as thermal, LiDAR, or multispectral) require high-bandwidth RF communication to send video feeds or sensor data back to the ground station.
Learn more about Optical Delay Line Solutions.
Payload Data: UAVs used for specific tasks like delivery or surveillance may need to transmit payload-related data, such as GPS coordinates, images, or diagnostic information.
Given the variety of data types and the need for real-time communication, a robust and reliable RF communication system is essential for the successful operation of drones in both civilian and military applications.

RF Communication Technologies for Drone-UAVs
The communication requirements of drones are diverse, necessitating different RF communication technologies and frequency bands. These technologies are designed to address challenges such as range, interference, data rate, and power consumption.
1. Frequency Bands
The RF spectrum is divided into several frequency bands, and each is used for different types of communication in UAV systems. The most commonly used frequency bands for drone communications are:
2.4 GHz: This band is one of the most popular for consumer-grade drones. It offers a good balance of range and data transfer speed, although it is prone to interference from other wireless devices (such as Wi-Fi routers and Bluetooth devices).
5.8 GHz: This band is often used for high-definition video transmission in drones, as it offers higher data rates than 2.4 GHz, but with a slightly shorter range. It’s less crowded than 2.4 GHz and typically experiences less interference.
Sub-1 GHz (e.g., 900 MHz): This frequency is used for long-range communications, as lower frequencies tend to travel farther and penetrate obstacles more effectively. It’s ideal for military drones or those used in remote areas.
L, S, and C Bands: These bands are used in military and commercial UAVs for long-range communication, often for surveillance, reconnaissance, and tactical operations. These frequencies have lower susceptibility to interference and are better suited for higher-power transmissions.
2. Modulation Techniques
The RF communication system in drones uses different modulation techniques to efficiently transmit data. Modulation refers to the method of encoding information onto a carrier wave for transmission. Some common modulation techniques used in UAV RF communication include:
Frequency Modulation (FM): Often used in control signals, FM is simple and efficient, providing clear communication with minimal interference.
Amplitude Modulation (AM): Used for video and lower-bandwidth applications, AM transmits a signal whose amplitude is varied to carry the information.
Phase Shift Keying (PSK) and Quadrature Amplitude Modulation (QAM): These more advanced techniques allow for high data transfer rates, making them ideal for transmitting high-definition video or large sensor datasets.
3. Signal Encoding and Error Correction
To ensure that RF communication remains stable and reliable, especially in noisy or crowded environments, drones use advanced signal encoding and error correction methods. These techniques help to mitigate the impact of signal interference, fading, and packet loss. Common methods include:
Forward Error Correction (FEC): This involves adding redundant data to the so that errors can be detected and corrected at the receiver end.
Diversity Reception: Drones may employ multiple antennas or receivers, allowing them to receive signals from different directions and improve the overall reliability of communication.
Spread Spectrum Techniques: Methods like Frequency Hopping Spread Spectrum (FHSS) or Direct Sequence Spread Spectrum (DSSS) spread the signal over a wider bandwidth, making it more resistant to jamming and interference.
4. Long-Range Communication
For long-range missions, RF communication technology needs to go beyond traditional line-of-sight communication. To achieve this, drones can leverage various technologies:
Satellite Communication (SATCOM): When beyond-visual-line-of-sight (BVLOS) operations are required, drones can use satellite links (via L, S, or Ku-band frequencies) to maintain constant communication with the ground station.
Cellular Networks: 4G LTE and 5G networks are increasingly being used for drone communication, especially in urban environments. 5G, in particular, offers ultra-low latency, high-speed data transfer, and extensive coverage.
Mesh Networking: Some UAVs can form mesh networks where each drone communicates with others in the fleet, extending the range of the communication system and providing redundancy.
Challenges in Drone-UAV RF Communication
While RF communication is essential for UAVs, it presents several challenges that need to be addressed to ensure the reliable and secure operation of drones.
1. Interference and Jamming
One of the biggest threats to RF communication in drones is interference from other electronic systems or intentional jamming. Drones, especially in crowded or military environments, must be capable of avoiding interference from various sources, such as:
Other drones operating on the same frequencies.
Wireless communication systems like Wi-Fi or Bluetooth.
Intentional jamming by adversaries in conflict zones or hostile environments.
To mitigate these issues, drones use frequency hopping, spread spectrum techniques, and advanced error-correction algorithms to make communication more resilient.
2. Limited Range and Power Constraints
The effective range of RF communication in drones is limited by factors such as transmitter power, antenna design, and frequency band characteristics. While UAVs with longer ranges can use lower frequencies like 900 MHz or satellite links, they are often limited by battery life and payload capacity.
The trade-off between range and power consumption is an ongoing challenge. Drones must find a balance between maintaining communication and extending their operational flight times.
3. Security Risks
The RF communication channel is vulnerable to security threats, such as signal interception, spoofing, and hacking. Unauthorized access to the communication link could compromise the integrity of the UAV’s operations or allow malicious actors to take control of the drone.
To secure drone communications, encryption methods like AES (Advanced Encryption Standard) and TLS (Transport Layer Security) are employed, ensuring that only authorized parties can decrypt and interpret the transmitted data.
4. Latency and Data Throughput
For applications that require real-time control and feedback, such as autonomous drones or those used in first-responder scenarios, low-latency communication is crucial. High latency could delay mission-critical decisions, especially in dynamic environments like search and rescue operations or military engagements. Additionally, high-data-throughput applications like video streaming require RF systems with robust bandwidth management.
Future Trends in Drone-UAV RF Communication
As UAV technology continues to advance, so will the communication systems that power them. Key trends in the future of drone RF communication include:
5G and Beyond: The rollout of 5G networks is expected to revolutionize drone communications with ultra-low latency, high bandwidth, and greater network density. This will enable more drones to operate simultaneously in urban environments, enhance remote operation, and facilitate advanced applications such as drone swarming and real-time video streaming.
Artificial Intelligence (AI) for Dynamic Communication: AI-powered algorithms can optimize communication links based on environmental conditions, such as avoiding interference, adjusting frequencies, and ensuring maximum data throughput. AI will also play a role in improving autonomous decision-making for UAVs in communication-heavy operations.
Integration with IoT: Drones are increasingly integrated into the Internet of Things (IoT) ecosystem. As a result, drones will not only communicate with ground control but also with other devices and systems in real-time. This opens new possibilities for industrial applications like smart farming, precision delivery, and environmental monitoring.
RF communication is at the heart of every drone’s operation, whether for military, industrial, or commercial use. As UAV technology continues to evolve, so too must the communication systems that support them. RF communication technologies are enabling drones to perform increasingly complex tasks, from surveillance and reconnaissance to logistics and environmental monitoring.
Despite the challenges posed by interference, range limitations, and security risks, advances in RF technology, coupled with innovations like 5G and AI, promise to take UAV communication systems to new heights—fostering more reliable, secure, and efficient operations across a range of industries.
-
3D Technology3 years ago
3D Scanner Technology for Android Phones: Unleashing New Possibilities
-
Business Solutions2 years ago
Understanding A2P Messaging and the Bulk SMS Business Landscape
-

 Business Solutions2 years ago
Business Solutions2 years agoThe Power of Smarts SMS and Single Platform Chat Messaging
-

 Automotive3 years ago
Automotive3 years agoDSRC vs. CV2X: A Comprehensive Comparison of V2X Communication Technologies
-
Tech3 years ago
On Using Generative AI to Create Future-Facing Videos
-

 Business Solutions2 years ago
Business Solutions2 years agoExploring OTP Smart Features in Smart Messaging Services
-

 Business Solutions2 years ago
Business Solutions2 years agoLive Video Broadcasting with Bonded Transmission Technology
-

 Business Solutions10 months ago
Business Solutions10 months agoThe Future of Healthcare SMS and RCS Messaging







