Cybersecurity
Reasons To Think About Identity Theft Protection
We are living in a digital world, where everything is handled on a digital basis. Digital potentials indeed have its boon and bane that we need to understand when we are dealing with it. One of the reformed ways in which digitalization has blessed us is digital identity. Through biometric and facial recognition, you can establish your identity and perform the necessary task.
Digital Identification Paves the Way for Identification Theft
Today biometric and facial recognition has become a crucial part of identification. Whether it is for your professional or personal use, you cannot avoid it. With the increasing use of facial recognition and faces being registered on multiple devices, the chances for identity theft becomes common. Some hackers can easily get access to the facial data and make use of it adversely. That’s when you should think about enhanced identity theft protection.
What You Need to Understand About Identity Theft Protection?
You will never know on how many platforms your digital identity lies that makes it prone to theft and breaches. Hackers are continually looking for opportunities to make use of that data and conduct a theft. Enhanced identity theft protection is a range of services that will help in securing your digital identity. For instance, your facial ID has some important biometric data that can be misused, so you need to adopt anti facial recognition that protects your facial ID with a password or other protection tools.
Why Do You Need Identity Theft Protection?
As a growing cyber-crime, identity theft needs to be addressed in an efficient manner; there are more than one reasons to adopt the services of identity theft protection. If you are still confused, take a look at the below reasons why you need it right now.
Protecting Your Financial Interests
Today facial IDs are used for financial services as well, as you need to verify your facial ID before making a transaction. Just think about the detrimental losses that you might have to suffer if your facial identity is misused by a hacker. Rather than looking for preventive methods, it is better to take the precaution and seek theft protection services. Look for identity theft protection services that can provide you with all-encompassing services like secure face authentication, video anonymization, and photoprotection.
Enhance Customer And Employee Loyalty
If you are a business entity, your employees and customer protection should be paramount for you. Using identity theft protection means for employees’ and customers’ identity, you will automatically create a sense of loyalty and trust among them. It will boost the morale of your employees and increase your customers’ experience with you. It will also enhance the credibility of your company and enable you to emerge as a tech-oriented and secure business organization.
Secured Personal Data
Right from your high school marks, to your ATM card details, everything is on the internet today that can access through your digital identity. It is imperative to safeguard your facial ID as it contains plenty of biometrics ID. The damage caused by identity theft can indeed be detrimental to your professional and personal life. Hence, you need to think wisely and look for services that can completely secure your identity and safeguard you from possible thefts.
Identity Theft Protect Service Providers Are The Solution For All
You cannot predict data breaches and identity theft, but you can definitely add a protective layer to your identity. That’s what identity theft protection services do for you. These service providers will look into your matter and provide you with an adequate theft protection solution that can best address your concern. Just seek out for some credible names in the industry that have already established a prominent place with their eminent services.
The Bottom Line
There’s no doubt in asserting that identity theft is one of the growing cybercrimes that needs to be controlled. You cannot possibly control how your facial data is perceived on a platform, but you can definitely protect your facial ID.
With identity theft protection, you can secure your photos, facial ID and even videos from getting breached and used for illegal activities. Whether you are a professional or a business entity, you would need the services of identity theft protection and its sub-services like anti facial recognition to protect your identity.

Cybersecurity
Microsoft Power Platform Security: The Risks You Cannot See and How to Address Them
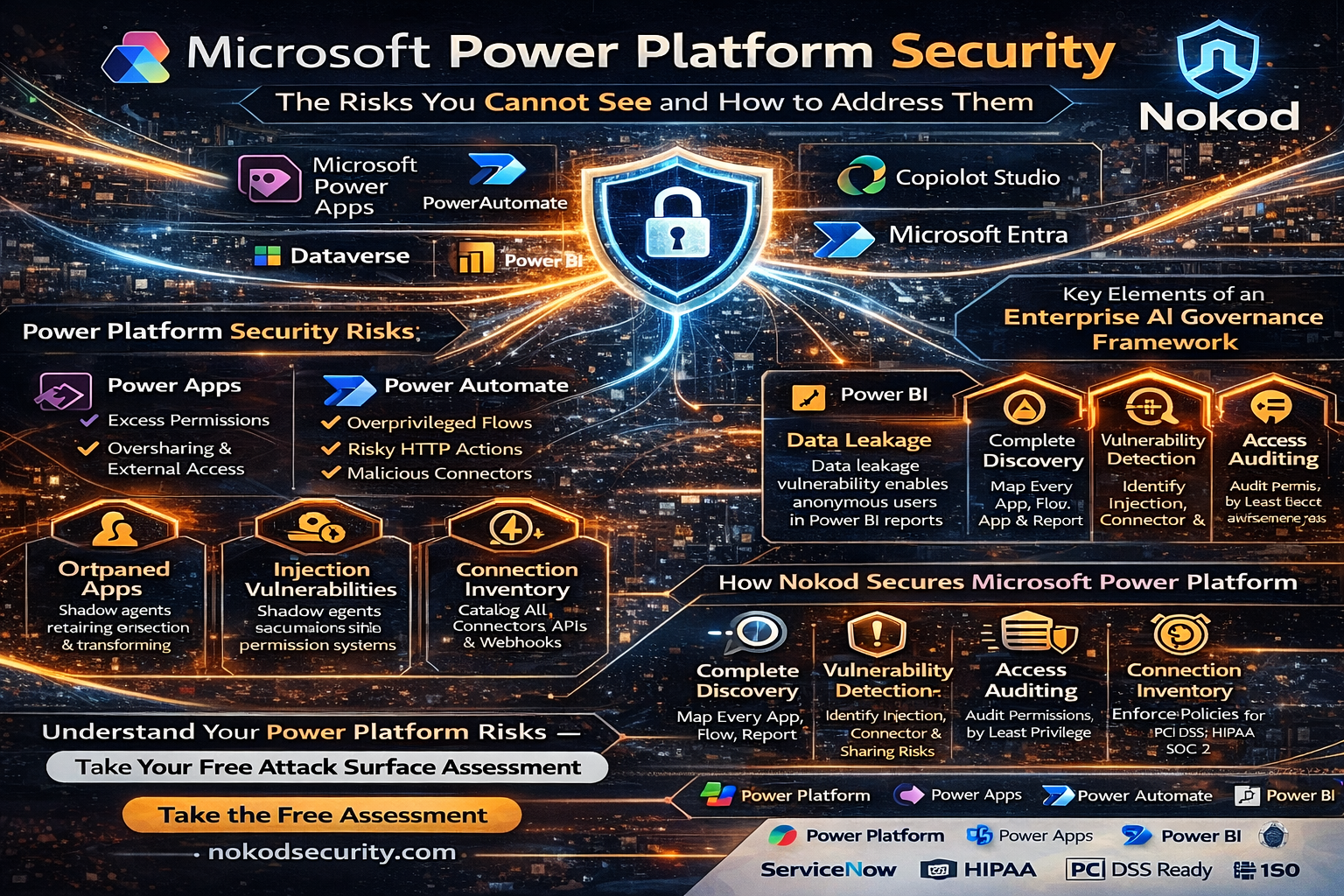
Microsoft Power Platform has become the backbone of citizen development across enterprises worldwide. Power Apps, Power Automate, Power BI, and Copilot Studio collectively enable millions of business users to build applications, automate workflows, analyze data, and deploy AI agents – all without writing code. But the same capabilities that make Power Platform indispensable also make it one of the most significant unmanaged security risks in the modern enterprise. This article examines the security challenges specific to Microsoft Power Platform and explains how Nokod Security addresses them.
Why Microsoft Power Platform Creates a New Security Paradigm
Power Platform is not a single product. It is an integrated ecosystem of tools that share a common data platform (Dataverse), a common connector framework, and a common identity model (Microsoft Entra). When a citizen developer builds a Power App that calls a Power Automate flow that reads from SharePoint and writes to SQL Server, they are creating a multi-system data pathway that traditional AppSec tools are entirely blind to.
The challenge is amplified by scale. According to Nokod, the average enterprise contains more than 10,000 business-built apps. A significant proportion of these are Power Platform applications and flows. Twenty percent of no-code apps are exposed externally. The gap between what security teams think they have and what exists in reality is one hundred percent.
Power Platform Security Risks: What Security Teams Need to Understand
The security risks within Microsoft Power Platform span all three major components:
Power Apps
- Apps built with excess permissions that allow access to sensitive Dataverse tables beyond what users need
- Apps shared tenant-wide or externally, making internal data accessible to unauthorized users
- Orphaned apps retaining connections and permissions after their creator has left the organization
- Injection vulnerabilities embedded in app logic that processes user input
Power Automate
- Flows that run under service accounts with overprivileged access to critical systems
- Unencrypted HTTP actions sending sensitive data to external endpoints
- Malicious third-party connectors embedded in automation workflows
- Flows triggering unauthorized actions in downstream systems like ERPs and CRMs
Power BI
The Nokod Research Team discovered a significant data leakage vulnerability in the Microsoft Power BI service affecting potentially tens of thousands of organizations. The issue relates to the relationship between Power BI report objects and their underlying semantic models. When a Power BI report is shared with users, all raw data represented by the underlying semantic model is also accessible to those users – including detailed data records that are used only for aggregations in the report UI. This means anonymous viewers may be able to access sensitive data, including employee data, business data, PHI, and PII, even when the report is not intended to surface that information.
Nokod reported the finding to the Microsoft Security Response Center (MSRC) and created a free Power BI Analyzer tool to help organizations assess their exposure to this vulnerability.
How Nokod Secures Microsoft Power Platform
Nokod Security offers a free attack surface assessment tool for Microsoft Power Platform, allowing organizations to immediately understand the scope of their exposure before committing to a full deployment. The full Nokod platform integrates with the Power Platform environment within minutes, using the native API to deliver comprehensive visibility across all apps, flows, and connected services.
Key capabilities for Power Platform security include:
- Complete discovery of all Power Apps, Power Automate flows, and Power BI reports across the tenant
- Inventory of all connections and connectors, including third-party and custom connectors
- Vulnerability detection for injection attacks, insecure HTTP calls, risky webhooks, and malicious integrations
- Access and permission auditing, including identification of excess permissions and oversharing
- Governance policy management with automated remediation and developer-friendly guidance
- Compliance monitoring for regulatory requirements including PCI DSS, HIPAA, and SOC 2
Power Platform Security and the Broader Enterprise LCNC Landscape
Power Platform rarely exists in isolation within an enterprise. It connects to SharePoint, Teams, Dataverse, Azure services, Salesforce, ServiceNow, and dozens of third-party systems. Security governance that addresses only Power Platform leaves significant gaps.
Nokod’s approach is inherently multi-platform. By providing a single security and governance layer across all citizen-developed and AI-agent-built applications – regardless of the underlying platform — Nokod enables security teams to see the full attack surface and apply consistent policies across every environment.
Nokod is ISO-certified and SOC 2 compliant, and its management team includes founders of Imperva and SecuredTouch (now Ping Identity), bringing decades of application security expertise to the LCNC and AI-agent security space.
To get started with Power Platform security, visit Nokod Power Platform Security. For information on securing Copilot Studio within your Power Platform environment, see Nokod Copilot Studio Security. To explore the full platform, visit nokodsecurity.com.
Frequently Asked Questions
Q: What is Microsoft Power Platform?
A: Microsoft Power Platform is an integrated suite of low-code tools including Power Apps, Power Automate, Power BI, and Copilot Studio. It enables business users to build applications, automate workflows, analyze data, and deploy AI agents without professional development skills.
Q: What Power BI vulnerability did Nokod discover?
A: The Nokod Research Team found that sharing a Power BI report also exposes all underlying raw data in the semantic model — including data not shown in the report UI- to all users with access. This can include sensitive PII, PHI, and business data.
Q: Does Nokod offer a free assessment for Power Platform?
A: Yes. Nokod Security provides a free attack surface assessment tool for Microsoft Power Platform to help organizations quickly understand their exposure.
Q: How does Nokod integrate with Power Platform?
A: Nokod connects to Power Platform through its native API and can deliver visibility within minutes of connection, without requiring any agents or endpoint installations.
Q: What compliance standards does Nokod support for Power Platform?
A: Nokod helps organizations achieve compliance with PCI DSS, HIPAA, SOC 2, and other regulatory frameworks within their Power Platform environments. Nokod itself is ISO-certified and SOC 2 compliant.
Business Solutions
Automotive IDS (Intrusion Detection Software): Safeguarding the Future of Connected Vehicles

The evolution of connected vehicles, autonomous driving systems, and over-the-air (OTA) updates has transformed the automotive industry into a high-tech environment. While these advancements offer numerous benefits, they also introduce new cybersecurity vulnerabilities. As modern vehicles become more complex and interconnected, the need to protect them from cyber-attacks becomes ever more urgent. One of the critical solutions to address these threats is the integration of Automotive Intrusion Detection Software (IDS Automotive).
Automotive IDS is designed to monitor vehicle systems in real-time, detect malicious activities, and respond to potential cybersecurity threats. In an era where vehicles are increasingly targeted by cybercriminals, an effective IDS plays a pivotal role in safeguarding not just the vehicle’s software and hardware, but also the safety of drivers, passengers, and other road users.
What is Automotive Intrusion Detection Software (IDS)?
Intrusion Detection Software (IDS) is a security technology that monitors and analyzes the activities of a system to detect signs of unauthorized access or suspicious behavior. In the context of automotive cybersecurity, IDS focuses on identifying and preventing attacks on a vehicle’s electronic control units (ECUs), communication networks, and other critical systems.
An automotive IDS typically operates by detecting irregularities in vehicle behavior that could indicate a cyberattack, such as unusual data traffic, unauthorized commands, or abnormal sensor readings. It analyzes the vehicle’s internal network traffic, such as Controller Area Network (CAN) bus, Ethernet, and FlexRay protocols, for any signs of intrusion or tampering.
How Automotive IDS Works
Automotive IDS operates in much the same way as traditional intrusion detection systems used in IT security, with some key differences specific to the automotive context:
1. Data Monitoring:
Automotive IDS continuously monitors the internal communication networks of a vehicle, including the CAN bus, Ethernet, and other communication channels. These networks serve as the backbone for data transmission between the vehicle’s various ECUs (e.g., engine control, infotainment, braking, steering), sensors, and actuators.
2. Anomaly Detection:
IDS systems typically use anomaly-based detection techniques to identify abnormal behavior in vehicle communication patterns. By establishing a baseline for “normal” vehicle behavior, the IDS can flag any activity that deviates from this baseline. Examples of anomalies could include unexpected changes in sensor readings, unusual messages between ECUs, or abnormal network traffic patterns that may indicate a cyberattack.
3. Signature-Based Detection:
Some IDS systems also use signature-based detection, which compares vehicle behavior against known attack signatures or pre-defined patterns of malicious activity. These signatures are updated regularly to reflect emerging threats, ensuring that the IDS can detect even the most recent attack methods.
4. Response Mechanisms:
Upon detecting a potential intrusion or anomaly, the IDS can trigger predefined responses to mitigate the threat. This may involve logging the event for further investigation, sending alerts to the vehicle’s central control unit, or taking immediate action such as isolating affected ECUs or triggering a failsafe mode to ensure safety.
5. Integration with Vehicle Security Systems:
An automotive IDS is typically integrated with other vehicle security systems, such as firewalls, secure communication protocols, and encryption mechanisms. This multi-layered security approach enhances the vehicle’s ability to prevent, detect, and respond to cyber threats.

Why is Automotive IDS Important?
The importance of Automotive IDS cannot be overstated in today’s connected car ecosystem. The integration of increasingly sophisticated technologies, like Advanced Driver Assistance Systems (ADAS) and autonomous driving features, has expanded the attack surface for potential cybercriminals. Here are several reasons why Automotive IDS is crucial:
1. Protecting Critical Vehicle Functions:
Modern vehicles are highly dependent on complex electronic systems to manage safety-critical functions, such as braking, steering, and acceleration. A successful cyberattack on these systems could have catastrophic consequences. Automotive IDS helps prevent unauthorized access to these systems by detecting and responding to potential threats in real-time.
2. Early Detection of Cyber Threats:
Intrusion detection software is one of the best tools for identifying cyberattacks before they can do significant damage. Whether it’s a remote hacker attempting to gain control of a vehicle’s systems or a local attacker trying to exploit vulnerabilities, an IDS can alert the vehicle’s control systems to the presence of an attack, enabling timely countermeasures.
3. Mitigating Risks to Privacy:
Connected vehicles gather and share vast amounts of data, from GPS locations to personal preferences. Cybercriminals may target these data streams to compromise users’ privacy. Automotive IDS helps prevent data breaches by identifying suspicious activity on the vehicle’s communication channels.
4. Real-Time Monitoring and Response:
In contrast to traditional vehicle security solutions, which may only provide post-event analysis, IDS operates in real-time. This means that a vehicle’s security systems can immediately detect and respond to an ongoing attack, minimizing the potential damage and ensuring that the vehicle remains operational and safe.
5. Compliance with Regulatory Standards:
The automotive industry is subject to increasing regulatory scrutiny related to cybersecurity, including standards like ISO/SAE 21434 for automotive cybersecurity and the UN R155 regulation for vehicle cyber resilience. Implementing Automotive IDS can help manufacturers meet these regulatory requirements and demonstrate their commitment to vehicle safety and security.
Types of Automotive IDS
There are two main types of IDS that can be used in automotive cybersecurity:
1. Host-Based IDS (HIDS):
Host-based IDS operates on individual ECUs or control units within the vehicle. These systems monitor the specific behaviors of the vehicle’s hardware and software to detect intrusions. HIDS can track file integrity, system configurations, and application behavior, providing detailed insights into any changes that could indicate an attack.
2. Network-Based IDS (NIDS):
Network-based IDS monitors the vehicle’s communication networks, such as CAN and Ethernet, to detect unauthorized or suspicious network traffic. NIDS analyzes the flow of messages between ECUs, sensors, and other vehicle components, looking for signs of malicious activity or abnormal data exchanges.
In many cases, an automotive cybersecurity system will use a combination of both HIDS and NIDS to provide comprehensive coverage against cyber threats.
Challenges in Implementing Automotive IDS
While the benefits of automotive IDS are clear, the implementation of these systems comes with its own set of challenges:
1. Complex Vehicle Architectures:
Modern vehicles contain a vast array of ECUs, sensors, and communication networks, each with unique security needs. Designing an IDS system that can effectively monitor and protect all these components is complex and requires integration with the vehicle’s entire electronic ecosystem.
2. Real-Time Processing:
Given the critical nature of vehicle operations, IDS systems must be able to detect threats in real-time without causing delays or performance degradation. This requires high processing power and advanced algorithms capable of handling large amounts of data quickly and efficiently.
3. False Positives:
One of the challenges with any IDS system is minimizing false positives — situations where benign activity is mistakenly flagged as malicious. In automotive contexts, false positives can be particularly problematic, as they may cause unnecessary disruptions to vehicle operations or trigger incorrect safety measures.
4. Evolving Cyber Threats:
The cybersecurity landscape is constantly evolving, with new attack methods and vulnerabilities emerging regularly. Automotive IDS systems need to be updated continuously to stay ahead of these threats. This can require ongoing development and support to ensure that vehicles remain secure over time.
As the automotive industry embraces the future of connectivity and automation, the need for robust cybersecurity measures has never been more critical. Automotive Intrusion Detection Software (IDS) serves as a vital component in safeguarding vehicles from the growing threat of cyber-attacks. By detecting and mitigating potential intrusions in real-time, IDS helps protect not only vehicle safety and privacy but also the reputation of manufacturers in an increasingly security-conscious market. As automotive technology continues to advance, the role of IDS in ensuring the integrity of connected and autonomous vehicles will only become more important.
Cybersecurity
Israeli Cybersecurity Investments: Fueling Innovation and Growth
As cyber threats continue to increase in frequency and complexity, the need for robust cybersecurity measures has become more pertinent than ever. To combat these threats, companies worldwide are investing heavily in cybersecurity technologies and services. In recent years, Israel has emerged as a leading hub for cybersecurity innovation and expertise, attracting significant venture capital investments in the sector. In this blog post, we will explore how cybersecurity venture capital investments are fueling innovation and growth in Israel’s cybersecurity industry, and why this trend is likely to continue in the years ahead. We will also examine some of the most promising Israeli cybersecurity startups that have attracted significant investments and are poised to make a significant impact in the global cybersecurity market.

Israel has emerged as a global hub for cybersecurity, attracting significant investments and establishing itself as a leader in the field. The country’s thriving cybersecurity ecosystem is supported by a robust network of early-stage venture capital (VC) firms that fuel innovation and drive the growth of cybersecurity startups. In this article, we will explore the landscape of Israeli cybersecurity investments and the role played by early-stage venture capital.
Israel’s Reputation as a Cybersecurity Powerhouse
Israel has gained a well-deserved reputation as a cybersecurity powerhouse, known for its cutting-edge technologies and expertise. This reputation is bolstered by a combination of factors, including a strong focus on cybersecurity education, close collaboration between the military and the private sector, and a culture of innovation and entrepreneurship.
The Role of Early-Stage Venture Capital (VC) in Israel
Early-stage venture capital firms play a vital role in the Israeli cybersecurity ecosystem. These firms provide crucial funding, guidance, and support to cybersecurity startups in their early phases of development. By investing in promising companies, early-stage VCs help nurture innovation, accelerate product development, and enable startups to scale their operations.

Investments in Israeli Cybersecurity Startups
Israeli cybersecurity startups have attracted significant cybersecurity venture capital investments from both local and international investors. The country’s reputation for producing groundbreaking technologies and the success stories of previous cybersecurity startups have made it an attractive destination for venture capital firms and strategic investors.
Early-stage venture capital firms in Israel actively seek out cybersecurity startups with disruptive technologies and strong growth potential. These firms not only provide financial support but also leverage their extensive networks and industry knowledge to help startups navigate challenges, identify market opportunities, and connect with potential customers and partners.
Investment Trends and Areas of Focus
The investment landscape in Israeli cybersecurity is characterized by a diverse range of areas of focus. Some startups specialize in network security, while others focus on cloud security, application security, or IoT security. The growing demand for solutions in areas such as artificial intelligence (AI), machine learning (ML), and data protection has also attracted significant investments.
Q&A Section:
What are some notable succes
s stories in Israeli cybersecurity investments?
Israel has seen several notable success stories in the cybersecurity realm. Companies like Check Point Software Technologies, CyberArk, and Palo Alto Networks have emerged as global leaders in cybersecurity, with significant market presence and successful IPOs. These success stories serve as inspiration for aspiring cybersecurity startups and attract further investments in the industry.
How does the Israeli government support cybersecurity investments?
The Israeli government recognizes the strategic importance of cybersecurity and actively supports the industry. It provides various initiatives, grants, and tax incentives to promote research and development in cybersecurity. Additionally, the government collaborates with industry stakeholders to foster partnerships, encourage international collaborations, and promote Israel as a global cybersecurity hub.
Are there any unique challenges or opportunities for early-stage venture capital firms in Israel’s cybersecurity sector?
While the Israeli cybersecurity sector offers immense opportunities, it also comes with unique challenges. One challenge is the fierce competition to identify and invest in the most promising startups. With a vibrant ecosystem and a steady stream of innovative companies, early-stage venture capital firms need to carefully evaluate investment opportunities and build strong relationships with entrepreneurs to secure deals. However, the abundance of talent, strong support systems, and access to international markets make Israeli cybersecurity investments an exciting prospect for early-stage VCs.
-
3D Technology3 years ago
3D Scanner Technology for Android Phones: Unleashing New Possibilities
-
Business Solutions2 years ago
Understanding A2P Messaging and the Bulk SMS Business Landscape
-

 Business Solutions2 years ago
Business Solutions2 years agoThe Power of Smarts SMS and Single Platform Chat Messaging
-

 Automotive3 years ago
Automotive3 years agoDSRC vs. CV2X: A Comprehensive Comparison of V2X Communication Technologies
-
Tech3 years ago
On Using Generative AI to Create Future-Facing Videos
-

 Business Solutions2 years ago
Business Solutions2 years agoExploring OTP Smart Features in Smart Messaging Services
-

 Business Solutions2 years ago
Business Solutions2 years agoLive Video Broadcasting with Bonded Transmission Technology
-

 Business Solutions10 months ago
Business Solutions10 months agoThe Future of Healthcare SMS and RCS Messaging







